
Picture this shit: It's 3 AM, you're sitting in front of your computer with bloodshot eyes, trying to dissect the HTML of that sweet banking page you're trying to clone. You've been at it for hours, manually copying source code, downloading assets, fixing broken links. But no matter how hard you try, the fucking thing just won't load properly. The fonts are all janky, images return 403 errors, and the CSS is still broken as fuck.

Finally, after what feels like an eternity of debugging, you're done. The phisher looks decent enough - not perfect, but it'll fool most boomers. You upload it to your bulletproof hosting, fire up your email cannon, and start blasting.
Then BAM!
Within hours, your domain's flagged, your hosting provider yanks your shit offline, and all that work goes down the drain fast. Your beautiful phishing page is dead. Your dreams of easy money are crushed. Your time is wasted.
Sound familiar? Yeah, I thought so.
Here's the thing: as detection tools get more sophisticated, so should your approach. The days of copy-pasting HTML and praying to the fraud gods are over. Today, we're diving into the next generation of phishing - one that gives you maximum extensibility and obfuscation out of the box. Phishers that can adapt on the fly, features that weren't possible before, and automatically hiding from those pesky security scanners.
Welcome to the future, motherfuckers. Let's ride.
How Traditional Phishing Works
Before we jump into the sexy new shit, let's recap how most of you currently make phishing pages:
The Old School Method:
- Target Selection: You pick a juicy target - usually a bank, payment processor, or email provider. Something where credentials = money.
- Page Cloning: Using tools like HTTrack, Save Page WE, Singlefile, or just good ol' Ctrl+S, you download the target's login page. This gives you the HTML, CSS, maybe some JavaScript if you're lucky.

- Asset Wrangling: Now comes the painful part - fixing all the broken shit. Images that won't load, fonts that reference the original domain, JavaScript that phones home to mama. You spend hours replacing URLs, downloading assets, and basically performing digital surgery on this Frankenstein's monster of a webpage.
- Backend Setup: You slap together some PHP script (probably copied from a 2015 HackForums post) that captures credentials and either emails them to you or logs them to a text file like it's 2005.
- Deployment: Upload to whatever shitty free hosting or compromised WordPress site you can find, set up your domain (probably something like "amaz0n-security.tk"), and pray it stays up long enough to catch some fish.
- Distribution: Spam emails, SMS, social media DMs - whatever vector gets your link in front of victims.
The problem? This process is fucking tedious, error-prone, and the results are often shit.
The Twin Problems: Extensibility and Obfuscation
There are many problems of traditional phisher making, but there's two general ones:
Problem #1: Obfuscation (Or Lack Thereof)
Here's a fun fact: Right now, as you're reading this, thousands of bots are crawling the web looking for phishing pages. These digital bloodhounds sniff out HTML that matches known patterns - a PayPal logo here, a "Sign In" button there, boom, you're flagged.
Why is this so easy for them? Server-Side Rendering. When someone (or something) visits your phishing page, your server hands them the full HTML. Every element, every string, every suspicious form field - it's all there in plain text for bots to analyze. It's like trying to hide drugs by putting them in a transparent bag.
The security companies have massive databases of HTML fingerprints from legitimate sites. When your bootleg Bank of America page serves up HTML that's 95% identical to the real thing, their algorithms light up like a Christmas tree. Your domain gets blacklisted and your domain registrar and hoster gets automatically notified.
Problem #2: Extensibility (The Real Killer)
This is where traditional phishing really shows its age. Let's say you want to level up your game and make your phisher asynchronous. What's that mean? Instead of just capturing creds and bouncing, you want to:
- Capture the username/password to your panel
- Try them in real-time against the actual site
- When it triggers OTP, dynamically show an OTP request page
- Capture the OTP while the victim is still on your site
- Profit with full account access
You'd need to:
- Reverse engineer the site's authentication flow
- Extract and understand their JavaScript
- Rebuild their styling for your new OTP page
- Make it all work seamlessly together
Enter Next Generation Phishing
Now here's where shit gets interesting. What if I told you there's a way to automatically generate a fully extensible codebase from any website? Code that's inherently obfuscated from scanners, lets you add complex features with ease, and makes your phishers practically undetectable to traditional scanning methods?
Enter Orchids.app - an AI tool that doesn't just COPY websites, it fucking RECREATES them as a React codebase. Now look, there's a metric fuckton of clone and AI code gen tools out there, but I've had way more success with Orchids than any of the others. While other tools give you half-assed copies that break the moment you touch them, Orchids actually understands what the fuck it's looking at.
What Orchids.app Actually Does
Instead of giving you a shitty HTML file with broken assets, Orchids.app uses AI to:
- Analyze the target website visually
- Understand the structure and components
- Rebuild it from scratch as a modern React application
- Generate clean, organized code using Tailwind CSS and Shadcn UI
You get a fully functional React project that looks close to the original but is completely rebuilt from the ground up. It's like having an AI developer recreate the site for you, except this developer doesn't ask questions and works for free.
Extend It And Add Features (Your Phisher is Now AI-Ready)
Here's where shit gets REALLY spicy. Remember that OTP capture scenario that's impossible with traditional methods? With a React codebase, it becomes trivial.
But here's the real deal: This makes your phisher completely AI-ready. You can now add as many features as your criminal mind can dream up, tweak everything down to the pixel, and expand functionality infinitely. Something that's straight-up impossible with those ancient ripped scampages you've been fucking around with.
Why? Because ripped scampages are digital garbage - they're littered with code artifacts, hardcoded references to the original domain, obfuscated JavaScript that you can't understand or modify, and CSS that breaks the moment you breathe on it wrong. Try adding an OTP page to a ripped PayPal scampage and watch it fall apart faster than your alibis.
Want to get really nasty? Tell your AI IDE: "Add a component that mimics the bank's exact loading screens while we drain their account in the background." Boom - done in minutes. Try pulling that shit with a ripped scampage and you'll be debugging minified jQuery from 2012 until the heat death of the universe.
The extensibility is unlimited because you're working with modern, clean code instead of digital archaeology. You have a clean, modern codebase that any bootcamp graduate could work with - and more importantly, that AI tools can understand and modify seamlessly.
Obfuscation
Because Orchids.app generates a React application, your phishing page is no longer served as static HTML. Instead:
- Client-Side Rendering: The browser receives JavaScript that BUILDS the page dynamically. Scanners see JavaScript, not a recognizable HTML structure.
- Component-Based Architecture: Your login form isn't sitting there in plain HTML. It's generated by React components at runtime.
- Build-Time Obfuscation: You can use Vite plugins to further obfuscate during build time. Minification, tree-shaking, even custom obfuscation - it's all on the table.
Code:
<form action="login">Step-By-Step Demo
Alright, enough theory. Let's get our hands dirty and clone Amazon like the professional degenerates we are.
Step 1: Card an Orchids.app Subscription
First things first - you need an Orchids.app account. While they have a free tier, you want the premium shit for unlimited clones and better AI models. Fire up your favorite carding setup and hit that subscription. If you can't even card a $20/month SaaS subscription, you have no business making phishers.
Step 2: Target Acquisition
Navigate to Amazon's sign-in page
Take a screenshot or save the URL - you'll need it for Orchids.app.
Step 3: The Clone Wars
- Head to
Code:
orchids.app - Paste the Amazon URL or upload your screenshot
- Watch as the AI works its magic
Within seconds, you'll have a React project that looks damn near identical to Amazon's login page.
Step 4: Choose Your Weapon
Now there might some artifacts left to fix, but you've got two options for refining your clone:
Option A: Download and Use AI IDEs
Download the project and open it in Cursor or Windsurf. These AI-powered IDEs let you make changes with natural language. Just tell them "make the login button darker" or "fix the mobile layout" and watch the magic happen.
Option B: Use Orchids.app's Built-in Editor
Stay in Orchids.app and use their prompt feature. You can refine directly in the browser with commands like "match the exact BofA red color" or "add the security logo from the original."
Either way, you'll see a clean structure:
Step 5: Quick and Dirty Backend
Setting up a proper backend is covered in Part 2. For now, use webhook.site:
- Go to webhook.site
- Get your unique URL
- Ask Orchid to replace the form action with that URL
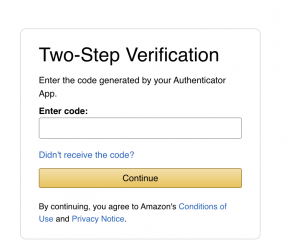
Step 6: Adding Advanced Features
Want to add OTP capture? Just show Orchids.app (or Cursor) a screenshot of Amazon's OTP page and say "add this as a new component." The AI will generate a component that automatically inherits all the Amazon styling - colors, fonts, spacing. It'll look native because your entire codebase is already themed correctly.
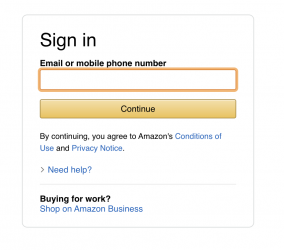
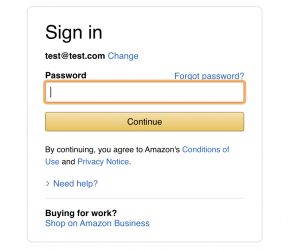
Then look at this feature addition that took me 2 minutes to implement:
Step 7: Build and Deploy
Code:
npm run buildThis generates an optimized, obfuscated production build.
For hosting? Just make a new Cloudflare Pages project, upload the
Code:
dist
The built files are minified JavaScript. No obvious HTML forms for scanners to detect. Just compiled React code that could be any web app! In the next guide we will use CF workers as your backend.
Caveats (This is Just the Beginning)
Now, before you run off thinking you're hot shit with your new AI-powered phishing kit, let me burst your bubble a bit - but also give you something to get excited about.
This is just a proof of concept. Apps like Orchids.app (and others like Same.Dev, MagicPath.AI, etc) are impressive, but they're not magic. The AI won't nail the clone perfectly on the first shot. You'll likely get:
- Missing interactive elements
- Slightly off colors or spacing
- Broken responsive design on some screen sizes
- Missing hover states or animations
- "Make the login button match the original shade of red"
- "Add the dropdown menu that appears on hover"
- "Fix the mobile layout to stack vertically"
But here's the fucking beautiful part: This is just the starting line, not the finish. AI is evolving at breakneck speed. What takes 5-10 iterations today will take 2-3 iterations in six months. What requires manual tweaking now will be automatic next year.
We're rapidly approaching a future where you'll paste a URL, hit enter, and get a pixel-perfect clone indistinguishable from the original. Every micro-interaction, every hover effect, every responsive breakpoint - all captured and recreated flawlessly in a single prompt. The AI will understand not just how a site looks, but how it behaves.
Think GPT-4 is smart? Wait until GPT-6 can analyze a website's entire user flow, understand its authentication logic, and recreate not just the visual design but the complete user experience. We're talking about AI that will reverse-engineer complex web apps and spit out production-ready phishing platforms that even the original developers couldn't tell apart.
This guide represents the first wave of truly intelligent phishing tools. By the time most script kiddies figure out how to use Orchids.app properly, the next generation of AI will make today's tools look like cave paintings.
Stay ahead of the curve, because this technology gap is only going to widen. The early adopters will feast while the dinosaurs still struggle with broken HTML copies.
Conclusion
The phishing game is evolving whether you like it or not. The old methods are becoming obsolete.
This is your wake-up call. The tools are here, the methods are proven, and the only thing standing between you and next-level phishing is your willingness to learn some basic React.
Most people will stick to their broken HTML copies. But for those willing to evolve and embrace the new tech, the rewards are there for the taking.
Remember: In this game, you're either innovating or you're getting caught.
Stay dangerous, stay learning, and for fuck's sake, use a VPN.
- d0ctrine out
P.S. - Part 2 will cover advanced techniques like automated personalization, defeating specific anti-fraud systems, and scaling your operation. If the feds haven't kicked down my door by then.



