- Joined
- 31.12.24
- Messages
- 16
- Reaction score
- 927

Picture this: Youre running fresh cards through $20/GB residential IPs. Your antidetect profiles tighter than a mob boss alibi. You triple-checked your setup - proxies cookies canvas noise everythings pristine.
But theres a digital rat in your operation you didnt spot: WebRTCs broadcasting your real IP address like a neon sign. No wonder every fucking order gets torched before the confirmation page loads - your browsers snitching to the antifraud systems through UDP packets.
The Digital Snitch
WebRTCs the overeager cop who cant keep his mouth shut. Designed for video calls its basically a protocol that lets browsers talk directly to each other without a middleman server. Before you understand how its leaking your real IP you first need to understand how the protocols that send and receive data over HTTP work:
TCP vs UDP
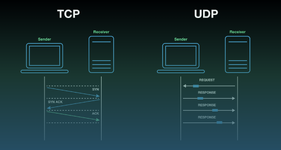
TCP and UDP are the two main protocols your browser uses to communicate with servers. TCP is like sending a certified letter - it requires acknowledgment at every step maintains order and follows all the rules. When you make a standard HTTP request through your proxy TCP politely routes everything through the proxys channels. Its reliable but slower perfect for when accuracy matters more than speed.
UDP is TCPs crackhead cousin. It doesnt give a fuck about delivery confirmation or proper channels - it just yeets packets at their destination through whatever path it finds. This makes it blazing fast for stuff like video calls but its a security nightmare. UDP packets will often bypass your proxy entirely taking the most direct route and exposing your real IP address.
WebRTCs UDP Trap
Heres where WebRTC fucks you over: its built to use UDP by default especially in Chrome. Think of it like a backdoor that completely ignores your security system.
Your proxy might handle regular HTTP traffic fine but WebRTC doesnt play by those rules. While your normal browsing traffic obediently flows through the proxy WebRTC connections will bypass it completely. They punch straight through it like a battering ram making direct connections that expose your real IP.
Even worse is that: most residential proxy providers dont support UDP traffic at all - theyre TCP-only paper shields that crumble the moment WebRTC starts sniffing around. So while your proxy dutifully routes your normal browsing WebRTCs making backdoor deals with STUN servers broadcasting your real IP to any site that asks.
How They Work Their Magic
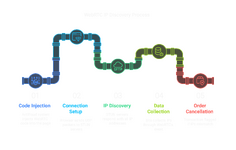
When a site with antifraud wants to sniff out your real IP through WebRTC heres the dirty process:
- Code Injection
The antifraud system injects invisible WebRTC code into their checkout page. This code pretends it wants to start a video call (spoiler: it fucking doesnt). - Connection Setup
Your browser being the helpful idiot it is immediately tries to establish that 'video call' connection:- Sends UDP packets to STUN servers
- Asks 'Whats my public IP address?' through multiple routes
- Bypasses your proxy because UDP gives zero fucks about your rules
- IP Discovery
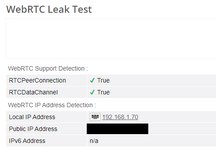
The STUN servers respond with ALL your IP addresses:- Your real IP (the one youre trying to hide)
- Your proxy/VPN IP (now useless)
- Any local network IPs
- Data Collection
The sites code harvests these IPs through WebRTCs `onicecandidate` event. Its like having a cop informant in your crew - everything you do gets reported back to HQ. - Order Cancellation
Once they have your real IP its game over. They compare it to your proxy IP location and flag any mismatches as fraud.
This whole process happens in milliseconds before you even finish typing your card details. Heck even before you even add anything to your cart. The antifraud system already knows youre full of shit before you hit submit.
Why A Lot of Proxies Are Dogshit
Heres something critical you need to understand: only SOCKS5 proxies support UDP traffic. HTTP proxies are TCP-only by design so dont waste your time trying to force UDP through them.
Once you got that out of the way your first step then obviously is to find a SOCKS5 proxy that actually handles UDP properly. But finding one that actually handles UDP properly is like finding an honest politician - they barely exist and the ones that claim they do are usually full of shit.
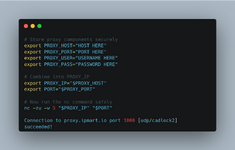
Code:
# Basic UDP check
nc -zv -u -w 3 your.proxy.ip 1080Run these checks on the terminal first to confirm that your proxy actually supports UDP or they are simply full of shit.
Chromiums Fatal Flaw
Now even if your proxy has UDP support most antidetect browsers completely botch their WebRTC implementation. This isnt just an antidetect problem - its been a core Chromium issue for years. Your precious Dolphin/Indigo/etc have a birth defect - their WebRTC stack gives zero fucks about proxy settings. Look at the bug report from way back in 2014:
Some antidetects like Linken that DO manage to spoof WebRTC leaks end up waving different red flags. Enable WebRTC spoofing and congrats - youve just made yourself stick out like a sore thumb to fingerprinting systems. Disable spoofing to blend in better and youre back to leaking IPs. Its a lose-lose game.
Firefox:
One slick way is to use Firefox as your antidetects browser. Since Firefox by default blocks WebRTC your session not having WebRTC enabled won;t be a red flag for the antifraud systems. Sounds perfect on paper - no leaks no config needed. But heres the reality check: Firefox users make up a tiny 3% slice of web traffic.
When youre trying to blend in with the crowd using a browser that 97% of people dont touch is like wearing a ski mask to the beach. Sure your IPs wont leak but youll stick out for a completely different reason. You need to weigh your options: risk WebRTC leaks with a Chromium-based browser or raise eyebrows with Firefoxs built-in protection.
How About VPNs?
VPNs are a whole different beast from proxies. While proxies fumble around at the application level VPNs tunnel EVERYTHING at the network layer. UDP TCP ICMP - doesnt matter it all goes through the encrypted tunnel. So using VPNs protects you from WebRTC leaks right off the bat.

But its not all sunshine and roses: You cant seriously use commercial VPNs for fraud right? This calls for a different approach: residential OpenVPN configs harvested from compromised devices. These configs give you:
- Perfect WebRTC protection (no leaks period)
- Residential IPs that blend right in
- Full UDP/TCP tunneling
- Zero fingerprinting red flags
So What The Fuck Do I Do?

After all that doom and gloom youre probably wondering if theres any fucking hope. Good news - where theres a will (and some technical know-how) theres always a way. Here are your options for dealing with this WebRTC clusterfuck:
- The Nuclear Option: Block WebRTC Completely

Remember that Firefox discussion? You can actually replicate that protection in any browser and antidetect browsers have this option. Some extensions even support blocking it. Blocking WebRTC guarantees sites wont see your real IP but it comes with a catch - your fraud score takes a slight hit. Most normies have WebRTC enabled so blocking it makes you stand out a bit. Still sometimes a slightly elevated fraud score beats a leaked IP.
- The System-Wide Solution: Proxy Chains + UDP Support
Instead of fighting with browser-level bullshit you can force ALL traffic through proxies at the system level. Tools like proxifier or custom iptables rules can wrap entire applications in proxy tunnels. The catch? Its a pain in the ass with antidetect browsers since it wraps everything to a single proxy. But for regular browsers like Safari on MacBook? Pure fucking gold. Safaris fingerprint is clean enough that with proper proxy chains youre practically invisible. Same with iOS devices which by default blocks WebRTC too.
- OpenVPN Configs
Like we already discussed residential VPN configs are also great for total WebRTC protection. When you tunnel everything through a compromised residential connection theres no leak to worry about - your real IP never touches the wire. The catch is finding legit configs that arent burned. But when you do? They work wonders for high-risk orders.
- Custom Bridge Software
Theres always some clever bastard selling solutions on Telegram - in this case custom software that acts as a bridge between your connection and forces all traffic (UDP or TCP) through your SOCKS5 proxy. Havent tested these myself so buyer beware. Could be the holy grail could be snake oil - do your own research before dropping cash.
Each method has its trade-offs. Blocking WebRTC is simple but suspicious. System-wide proxying works great but limits your browser choices. Custom solutions might be perfect or complete scams. Pick your poison based on your specific needs and risk tolerance.
Remember: Theres no perfect solution here. Security is always a game of trade-offs. The key is understanding the risks and benefits of each approach then choosing the one that best fits your operation.